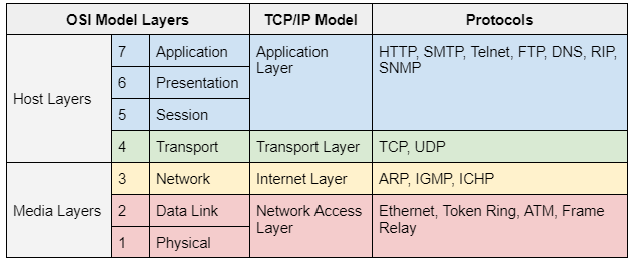
OSI (Open Systems Interconnection) is a model that provides common settings for the coordination of ISO standard development. It consists of 7 layers, remember: “Please Do Not Throw Sausage Pizza Away”
- Physical: The physical layer is responsible for the transmission and reception of unstructured raw data between devices in the form of bits, such as a network interface controller, Ethernet hub, or network switch, and a physical transmission medium. e.g. cable, RJ45
- Data Link: The data link provides transmission of data frames between two nodes connected by a physical layer in other words physical addressing e.g. MAC, switches
- Network: The network layer provides structuring and managing a multi-node network, including addressing, routing, and traffic control e.g. IP, routers
- Transport: The transport layer provides reliable transmission of data segments between points on a network, including segmentation, acknowledgment, and multiplexing, e.g. TCP, UDP, and port numbers.
- Session: The session layer creates the setup, controls the connections, and ends the teardown, between two or more devices. The session layer also provides for the full-duplex, half-duplex, or simplex operation, and establishes procedures for checkpointing, suspending, restarting, and terminating a session between two related streams of data, e.g. RTCP, PTP, PAP, ACK, RPCP, SDP.
- Presentation: The presentation layer provides translation of data between a networking service and an application, e.g. encryption/decryption, encoding, data compression, ASCII, PNG, MIDI, TLS.
- Application: The application layer is the top level in OSI. This layer provides high-level protocols for resource sharing or remote file access, e.g. Telnet, DHCP, SMTP, SNMP, NFS, HTTP, FTP, DNS.
TCP/IP model is a more concise network and consists of 4 layers, remember, “Armadillos Take In New Ants.”
- Network Access (or Link) corresponds to the OSI data link layer and may include some network layer protocols and similar capabilities to the physical layer.
- Internet performs functions as those in a subset of the OSI network layer.
- Transport (or host-to-host) maps to the OSI session layer and the OSI transport layer’s graceful close functionality.
- Application (or Process) corresponds to the OSI presentation layer, most of the session layer, and the application (or Process) layer.
Consideration for network and application security across OCI layers
- DDoS Protection: Preserves uptime despite any attack type or size. DDoS attacks are commonly on layers 3 (Network), 4 (Transport), 6 ( Presentation), and 7 (Application). Infrastructure layers attacks can occur in Network and Transportation layers. Application layer attacks can occur in the Presentation and Application layers.
- CDN: Use CDN to improve performance, cut hop and bandwidth costs, and cache static resources close to the edge.
- WAF: Web Application Firewall ( WAF) traffic control that allows legitimate traffic, protects applications by filtering and monitoring web traffics, and blocks unwanted traffic.
- Bot protection: identifies anomalies in bot behavior and traffic and validates them using a challenge mechanism so that it has no negative effects on users.
- API security: Finding vulnerable API endpoints and allowing only desired traffic
- Account protection: identifies and blocks attempts to hack into users’ accounts and use the information for malicious purposes.
- Atack analytics: analytics mitigate and respond to real cyber security threats
Reference:
